In case of DDoS attacks, cybercriminals use several compromised computers to target a particular resource. DDoS attackers are taking great things about internet\'s package data transfer technology the location where the data transferred from any source to any destination. White duck down is maligned by consumers on occasion because duck down has a far more noticeable odor with it versus white goose down. In layman terms, think about DOS hosting providers and protectors as a sponge that absorbs an excellent deal of water before it can even splash a of it on you.
The price of down can range from $2 dollars from grey duck feathers to $50 per pound for 800 fill power white goose down. Timely conviction of offenders is important to discourage Web crime. DDoS attacks on business websites may severely impact their productivity and lead to losses. The expense of down is influenced by supply and demand within the world so that when climates experience extra warm temperature ranges - jackets and bedding sales go down thus demand and price. It is projected that down and feather prices will never go back to their low ranges within the 90\'s ever.
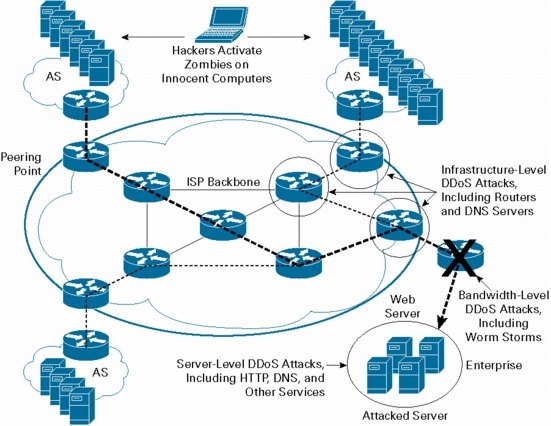
The Internet is definitely an unsafe place, with DDoS attacks rising as the bludgeon associated with preference for cyber hackers and international cyber terrorists and is adding up, with ever-more-powerful tools in the hacker\'s store. You simply must look for a DDOS hosting provider that are experts in DOS protection, prevention, and third-party filtration. There are several approaches which can assistance to prevent a DDoS attack.
There are a lot of methods you are able to use to fight, stop, and also prevent DDoS and DOS attacks. Multitudes of requests are sent simultaneously booter towards the targeted resource, which makes it virtually ddos impossible for that resource to supply normal services to the legitimate users. Some of the precautions are taken from company\'s servers to defend themselves in the data sent from contaminated PCs throughout the Internet. Who should be concerned with a DOS Attack?.
2FA or two factor authentication is an effective solution to prevent botnet attacks as it works well for overcoming vulnerabilities of your weak password. Federal Bureau of Investigation (FBI) has issued over booter forty search warrants throughout U. It is a thing that you have to get ready for emotionally and financially.
Cybercrime incidents are developing at an alarming rate. The higher the fill power of the down the further it travels through this series of walls. FBI is coordinating with law enforcement authorities of European nations to trace down the culprits. Down and feathers can\'t be more different in feeling, usage as well as prices. Users must install and regularly anti-malware programs to safeguard their computer systems against sophisticated cyber threats.
The Internet is surely an unsafe place, with DDoS attacks rising as the bludgeon of preference for cyber hackers and international cyber terrorists and is also adding up, with ever-more-powerful tools inside a hacker\'s store. Hard firewall helps though good fire walls are damn costly. Heavy or dense filling like feathers fall off within the beginning of the separating process, therefore they are typically cheaper.
Never forget to utilize a Firewall. Organizations should be proactive in identification and mitigation of security flaws. S as part in the inquiry. The networks are flooded with several facts requests creating complete disruption of solutions.
No comments:
Post a Comment